Simon Tomes
Community Lead at Ministry of Testing
Challenge Description
In this challenge, you’ll be provided with a system model diagram and some requirements (links below).
Your goal is to create a set of potential threats using the STRIDE Threat Model.
For example:
- Spoofing a person. A hacker takes over an account, impersonates someone from the hotel chain and sends a phishing message.
- Tampering with a network. A hacker modifies data flowing over the network and books 100 rooms on behalf of someone else instead of 1 room, just for the fun of it!
Use the following before and during the challenge:
- Restful Booker Platform System Model Diagram
- Restful Booker Platform Development Board (with Requirements)
What you’ll learn
- Use a model to rapidly create a set of potential threats
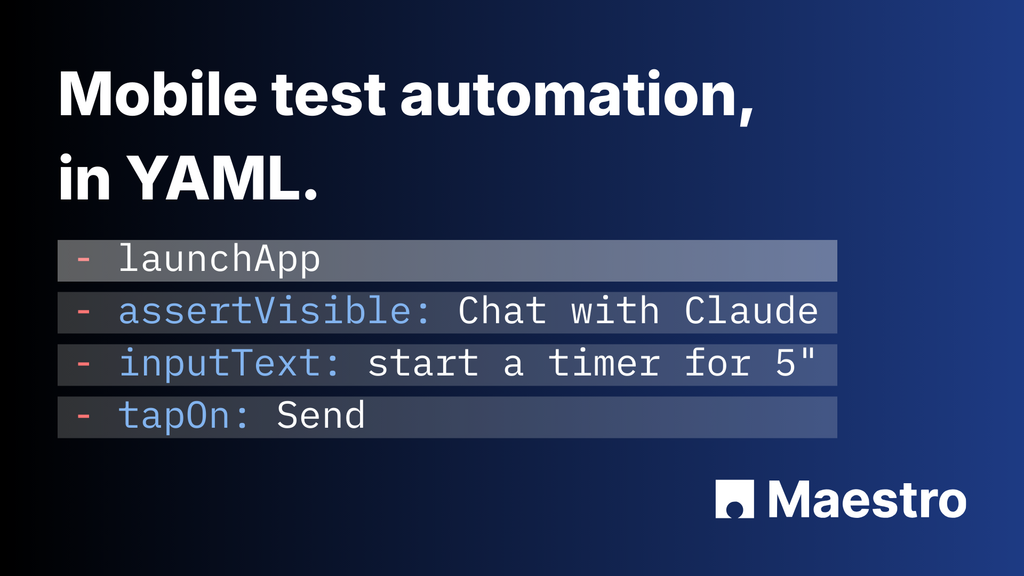
Create E2E tests visually. Get clear, readable YAML you can actually maintain.
Explore MoT


Mitigate security risks by building simple security testing techniques into your daily routine

Debrief the week in Quality via a community radio show hosted by Simon Tomes and members of the community