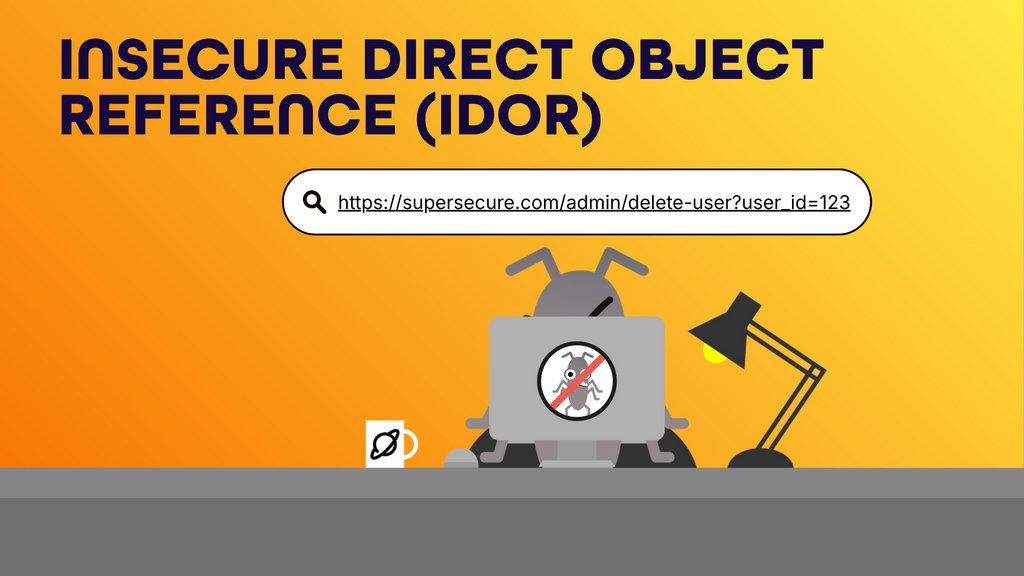
IDOR is when an application exposes internal objects (like user IDs, files, or records) in a way that lets users access data they shouldn’t, for example, by simply changing a value in the URL.
IDOR is one of the most common vulnerabilities found in bug bounty programs, probably “THE ONE” to know.
Example:
If a URL is
IDOR is one of the most common vulnerabilities found in bug bounty programs, probably “THE ONE” to know.
Example:
If a URL is
https://example.com/profile?user_id=123
And the application doesn’t verify if the user accessing the page is actually user 123; someone could change the user_id to 456 and access that user’s profile and edit it.