Activity
Richard Adams
Senior Test Analyst
He / Him
Passionate about quality & testing. Creator of Threat Agents card game and regularly found chatting cyber security.

thanked contributors on:

Anne explores how security testers differ from software testers

earned:

The Bittersweetness of Security Testing - Anne Oikarinen

awarded Anne Oikarinen for:

The Bittersweetness of Security Testing - Anne Oikarinen

thanked contributors on:

Evil User Stories - Improve Your Application Security - Anne Oikarinen

earned:

Evil User Stories - Improve Your Application Security - Anne Oikarinen

awarded Anne Oikarinen for:

Evil User Stories - Improve Your Application Security - Anne Oikarinen

awarded Anne Oikarinen for:

Evil User Stories - Improve Your Application Security - Anne Oikarinen

earned:

Evil User Stories - Improve Your Application Security - Anne Oikarinen

thanked contributors on:

Watch "TThreat Modelling: How Software Survives in a Hacker’s Universe" with Saskia Coplans from TestBash Manchester 2019

earned:

Threat Modelling: How Software Survives in a Hacker’s Universe Saskia Coplans

awarded Saskia Coplans for:

Threat Modelling: How Software Survives in a Hacker’s Universe Saskia Coplans

awarded Saskia Coplans for:

Threat Modelling: How Software Survives in a Hacker’s Universe Saskia Coplans

earned:

Threat Modelling: How Software Survives in a Hacker’s Universe Saskia Coplans

awarded Nicola Sedgwick for:

The Security Issue That Killed a Financial Product Launch - Nicola Sedgwick

earned:

The Security Issue That Killed a Financial Product Launch - Nicola Sedgwick

awarded Beth Marshall for:

The Average Tester: Succeeding Because You Are Not a Rockstar - Beth Marshall

earned:

The Average Tester: Succeeding Because You Are Not a Rockstar - Beth Marshall

awarded Venkat Ramakrishnan for:

Test Leadership In Requirements & Specification Stages

earned:

Test Leadership In Requirements & Specification Stages

awarded Caleb Crandall for:

Discussion - The Future of Test Cases

awarded Bedford West for:

Discussion - The Future of Test Cases

awarded Kim Nepata for:

Discussion - The Future of Test Cases

earned:

Discussion - The Future of Test Cases

awarded Gwen Diagram for:

99 Second Talks - TestBash Home 2021

earned:

99 Second Talks - TestBash Home 2021

awarded Jokin Aspiazu for:

Our Own QA Academy - Jokin Aspiazu

earned:

Our Own QA Academy - Jokin Aspiazu

awarded Louise Gibbs for:

Using Empathy To Guide An Exploratory Accessibility Testing Session

earned:

Using Empathy To Guide An Exploratory Accessibility Testing Session

awarded Lewis Prescott for:

User Driven Test Reports, Based on Feedback and Feelings

earned:

User Driven Test Reports, Based on Feedback and Feelings

earned:

Let’s Go Threat Modelling

awarded Nithin SS for:

The Hidden Logic of Thinking for Testers

earned:

The Hidden Logic of Thinking for Testers

awarded Lena Nyström for:

Would Heu-risk It?

earned:

Would Heu-risk It?

awarded Alex Reynolds for:

The Power of Habit

earned:

The Power of Habit

thanked contributors on:

Learn how to experiment with coaching with Clare Norman

earned:

Quality Coaching: Level 1

awarded Clare Norman for:

Quality Coaching: Level 1

earned:

Member visited TryHackMe

awarded Clare Norman for:

Quality Coaching: Level 1

earned:

Quality Coaching: Level 1

thanked contributors on:

Watch "Evolving Our Testing: Assessing Quality Throughout The SDLC" with Dan Ashby from TestBash UK 2022

earned:

Evolving Our Testing: Assessing Quality Throughout The SDLC

awarded Dan Ashby for:

Evolving Our Testing: Assessing Quality Throughout The SDLC

awarded Dan Ashby for:

Evolving Our Testing: Assessing Quality Throughout The SDLC

earned:

Evolving Our Testing: Assessing Quality Throughout The SDLC

awarded Callum Akehurst-Ryan for:

99 Second Talks - TestBash UK 2022 Day 1
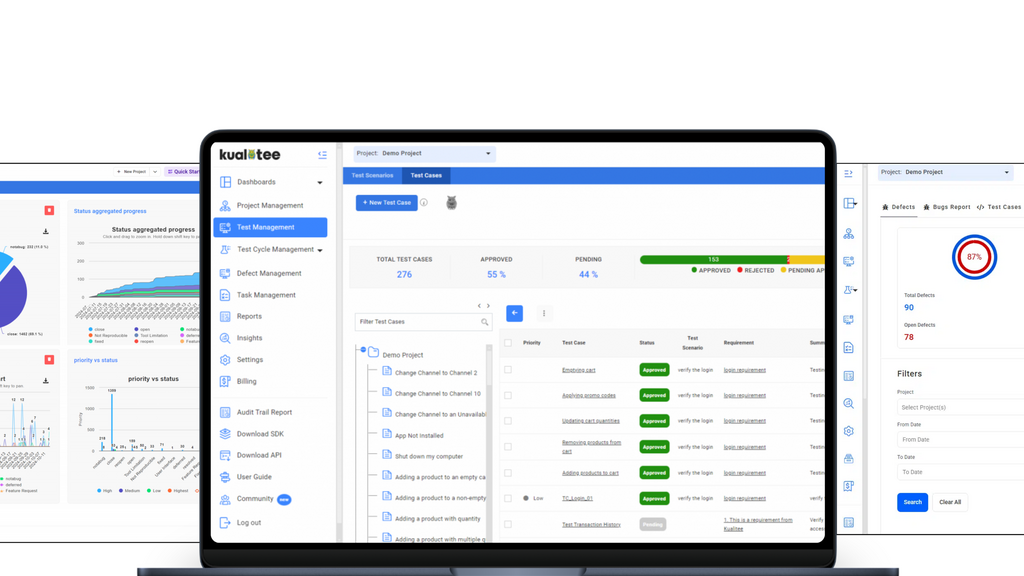
Manage your entire QA lifecycle in one place. Sync Jira, automate scripts, and use AI to accelerate your testing.
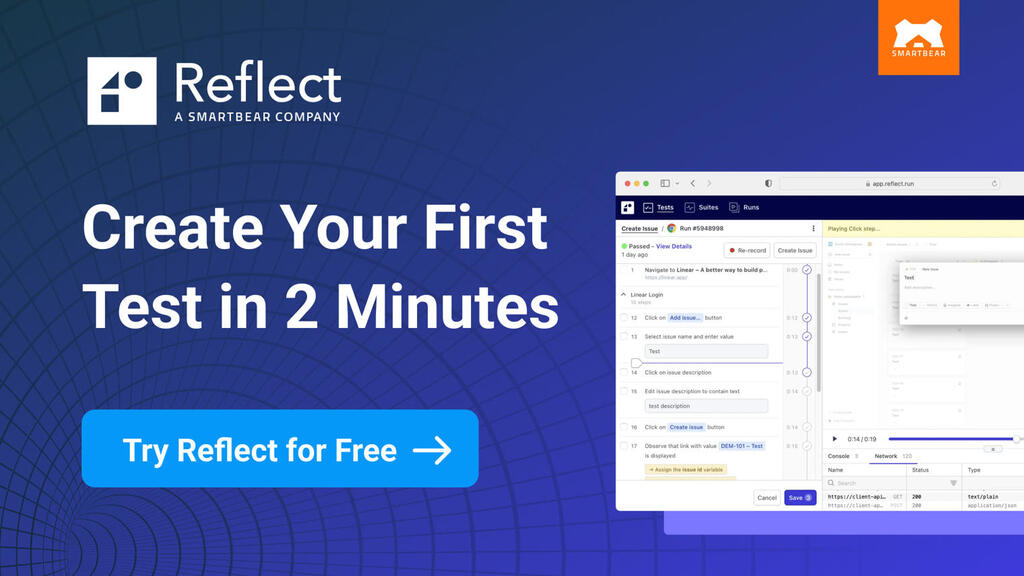
Create, run, and maintain web and mobile tests with no-code, AI-driven automation in the cloud

With servers in >250 cities around the world, check your site for localization problenms, broken GDPR banners, etc.

Jira Issue Connect brings live, real-time Jira data directly into TestRail, eliminating tab-switching and stale fields.
